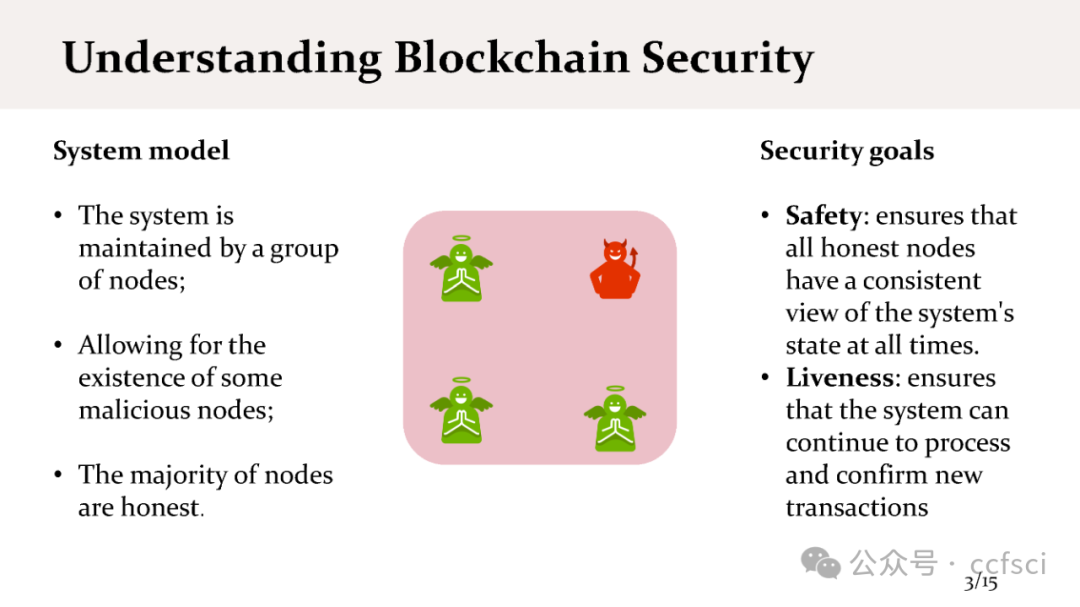
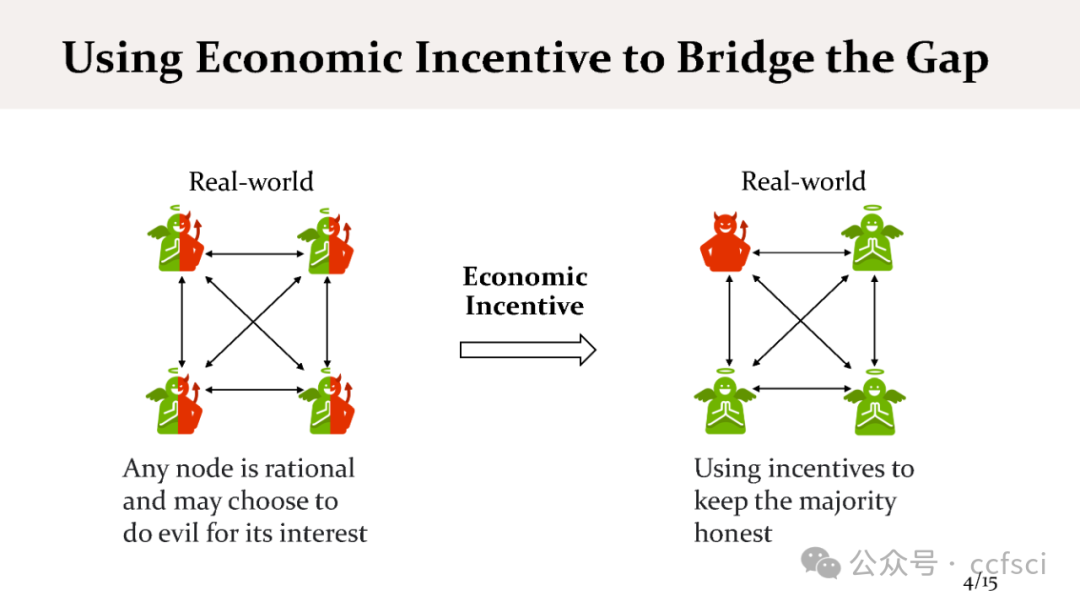
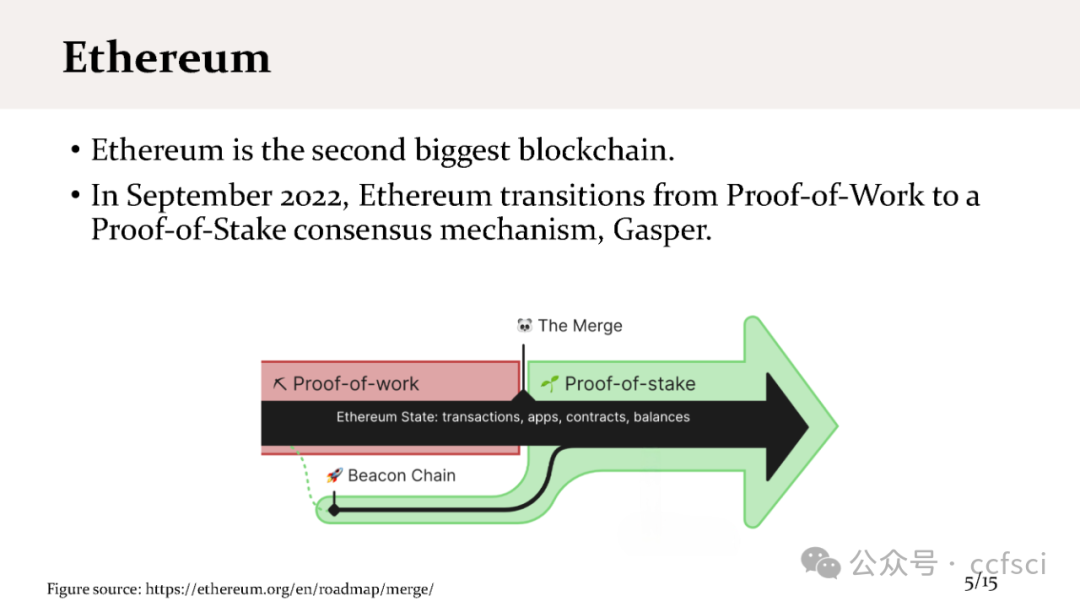
区块链论文速读A会-SECURITY 2024 如何攻击POS的激励机制 附ppt下载_max attestation matters: making honest parties los

Conference:33rd USENIX Security Symposium
CCF level:CCF A
Categories:network and information security
Year:2024
Conference time:August 14–16, 2024 Philadelphia, PA, USA
Title:
Max Attestation Matters: Making Honest Parties Lose Their Incentives in Ethereum PoS
Max Attestation很重要: 让诚实的各方在以太坊 PoS 中失去激励
Authors:

Abstract:
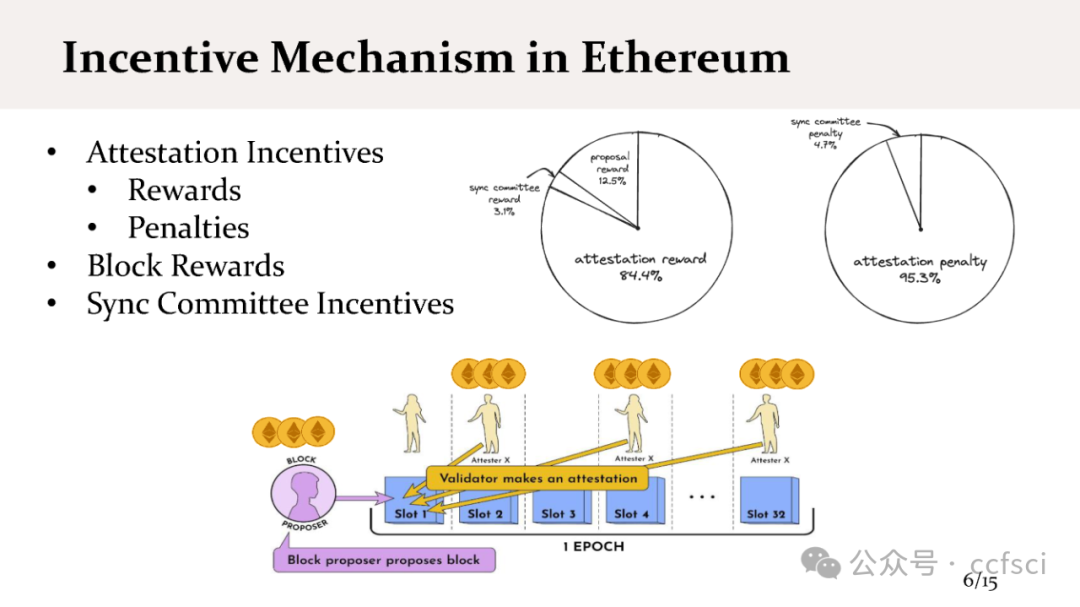
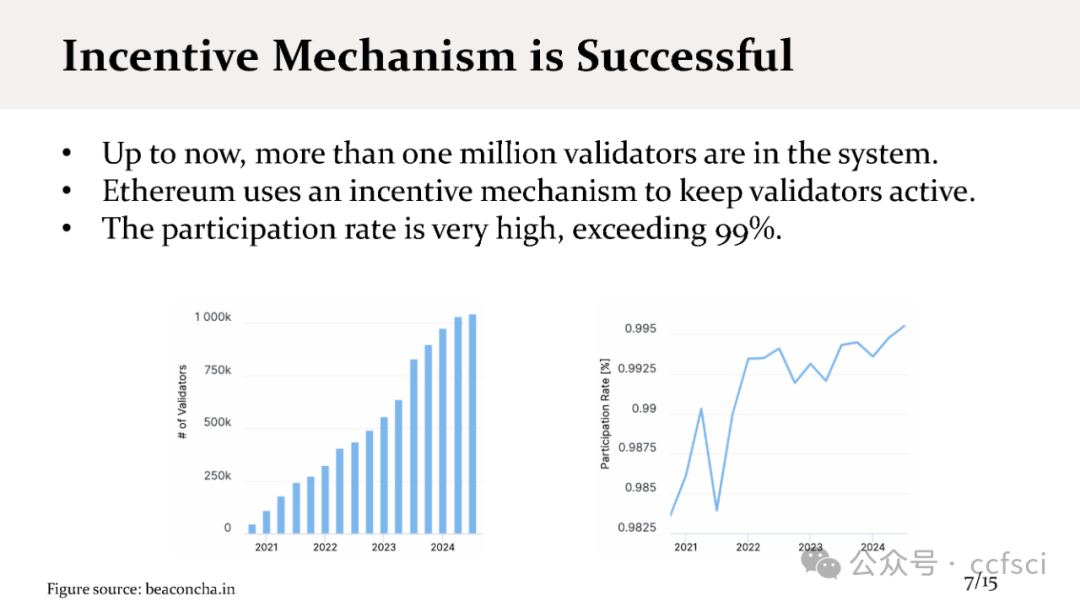
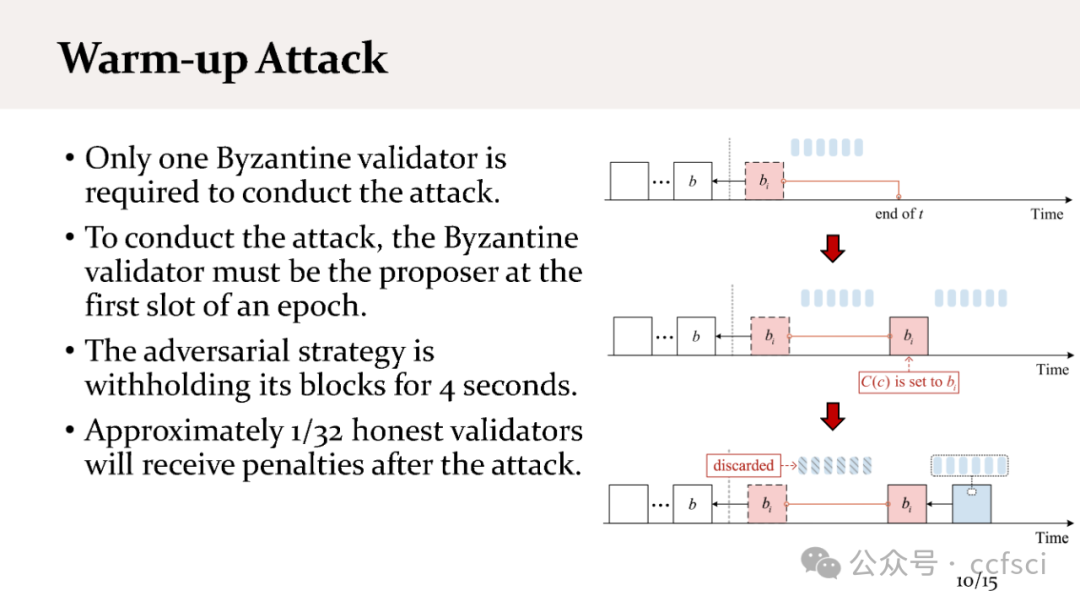
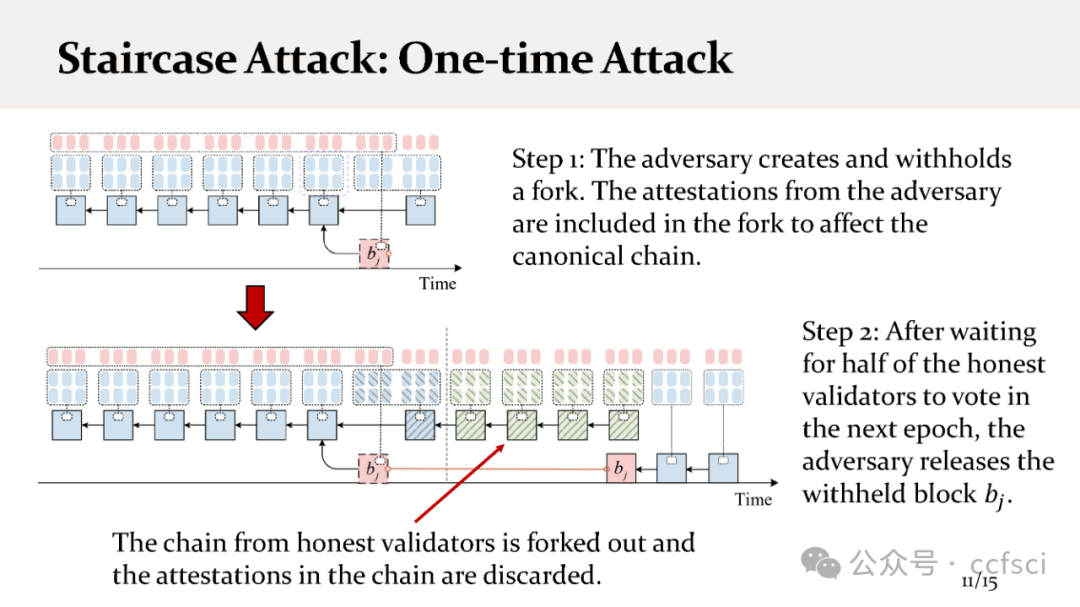
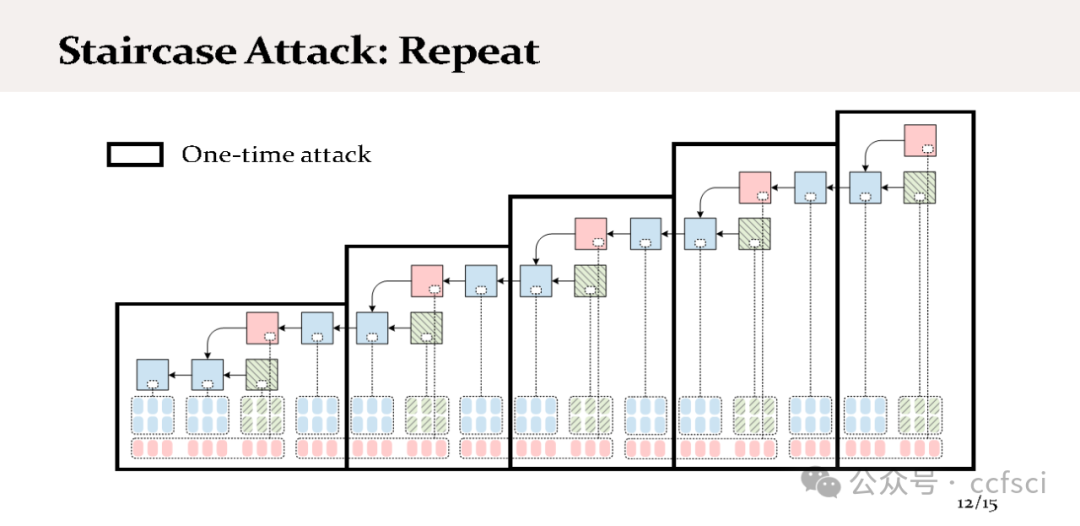
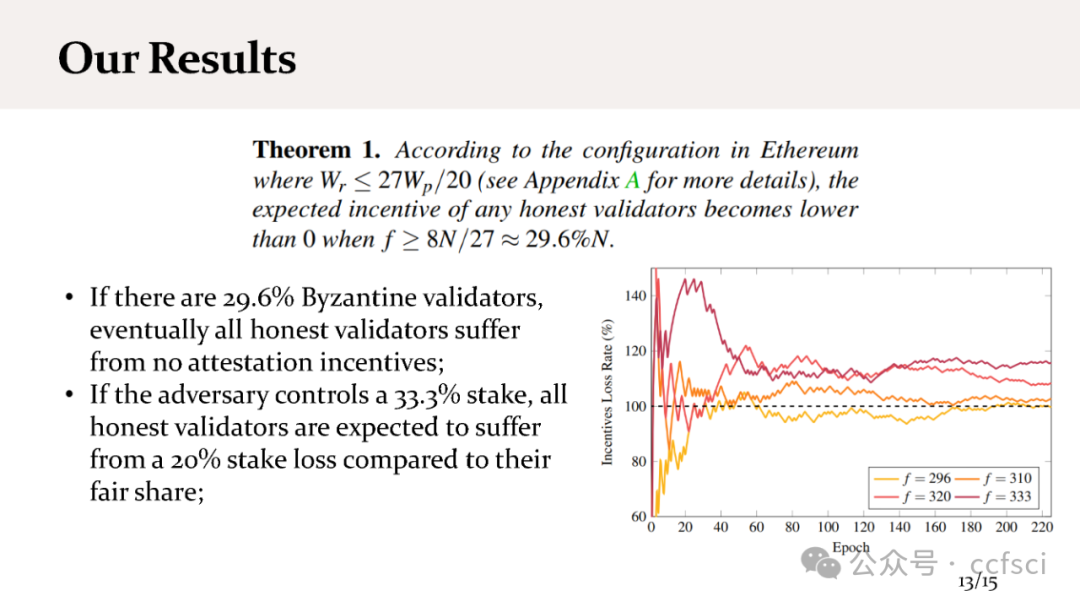
We present staircase attack, the first attack on the incentive mechanism of the Proof-of-Stake (PoS) protocol used in Ethereum 2.0 beacon chain. Our attack targets the penalty of the incentive mechanism that penalizes inactive participation. Our attack can make honest validators suffer from penalties, even if they strictly follow the specification of the protocol. We show both theoretically and experimentally that if the adversary controls 29.6% stake in a moderate-size system, the attack can be launched continuously, so eventually all honest validators will lose their incentives. In contrast, the adversarial validators can still receive incentives, and the stake owned by the adversary can eventually exceed the one-third threshold (system assumption), posing a threat to the security properties of the system.
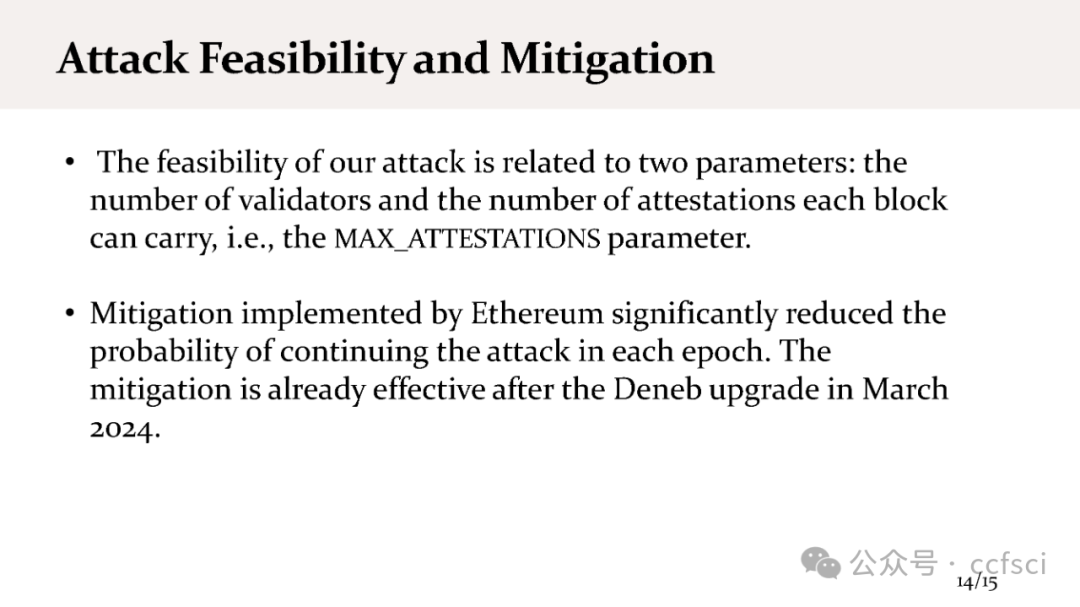
In practice, the attack feasibility is directly related to two parameters: the number of validators and the parameter MAX_ATTESTATION, the maximum number of attestations (i.e., votes) that can be included in each block. We further modify our attack such that, with the current system setup (900,000 validators and MAX_ATTESTATION=128), our attack can be launched continuously with a probability of 80.25%. As a result, the incentives any honest validator receives are only 28.9% of its fair share.
我们提出了阶梯攻击,这是对以太坊 2.0 信标链中使用的权益证明(PoS)协议激励机制的首次攻击。我们的攻击针对的是激励机制中惩罚不积极参与者的惩罚措施。即使诚实的验证者严格遵守协议规范,我们的攻击也会使他们受到惩罚。我们从理论和实验两方面证明,如果对手在一个中等规模的系统中控制了 29.6% 的股份,那么攻击就可以持续发起,因此最终所有诚实的验证者都会失去激励机制。相反,敌对验证者仍然可以获得激励,而且敌对验证者拥有的股份最终会超过三分之一的阈值(系统假设),从而对系统的安全属性构成威胁。
在实践中,攻击的可行性与两个参数直接相关:验证者的数量和参数 MAX_ATTESTATION,即每个区块中可包含的验证(即投票)的最大数量。我们进一步修改了我们的攻击,使得在当前系统设置(900,000 个验证者和 MAX_ATTESTATION=128)下,我们的攻击能以 80.25% 的概率连续发起。因此,任何诚实的验证者获得的奖励只有其公平份额的 28.9%。